1. Burp Suite is an integrated platform for attacking web applications. It contains a variety of tools with numerous interfaces between them designed to facilitate and speed up the process of attacking an application. All of the tools share the same framework for handling and displaying HTTP messages, persistence, authentication, proxies, logging, alerting and extensibility. There are two versions available including a free version and also Burp Suite Professional.It is a Java application that can be used to secure or penetrate web applications.The suite consists of different tools, such as a proxy server, a web spider, intruder and repeater.BurpSuite allow us to forward all of the web traffic from your browser through BurpSuite so that you can see each HTTP Request and Response and manipulate it to your heart’s content. This post will configure burp suite with Iceweasel in Kali Linux .
2. Open Internet - Iceweasel Web Browser
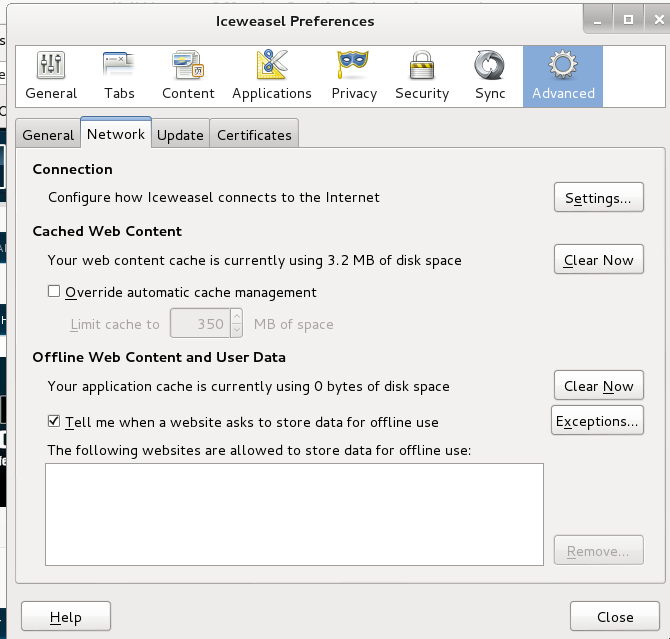
4. Preference Window will be open Now go to Advance → Network → Setting
5. Select Manual Proxy then set 127.0.0.1 in HTTP Proxy area and port should be 8080. Use this proxy server for all protocols by checking the box. Clear the No Proxy field then Finally Click OK.
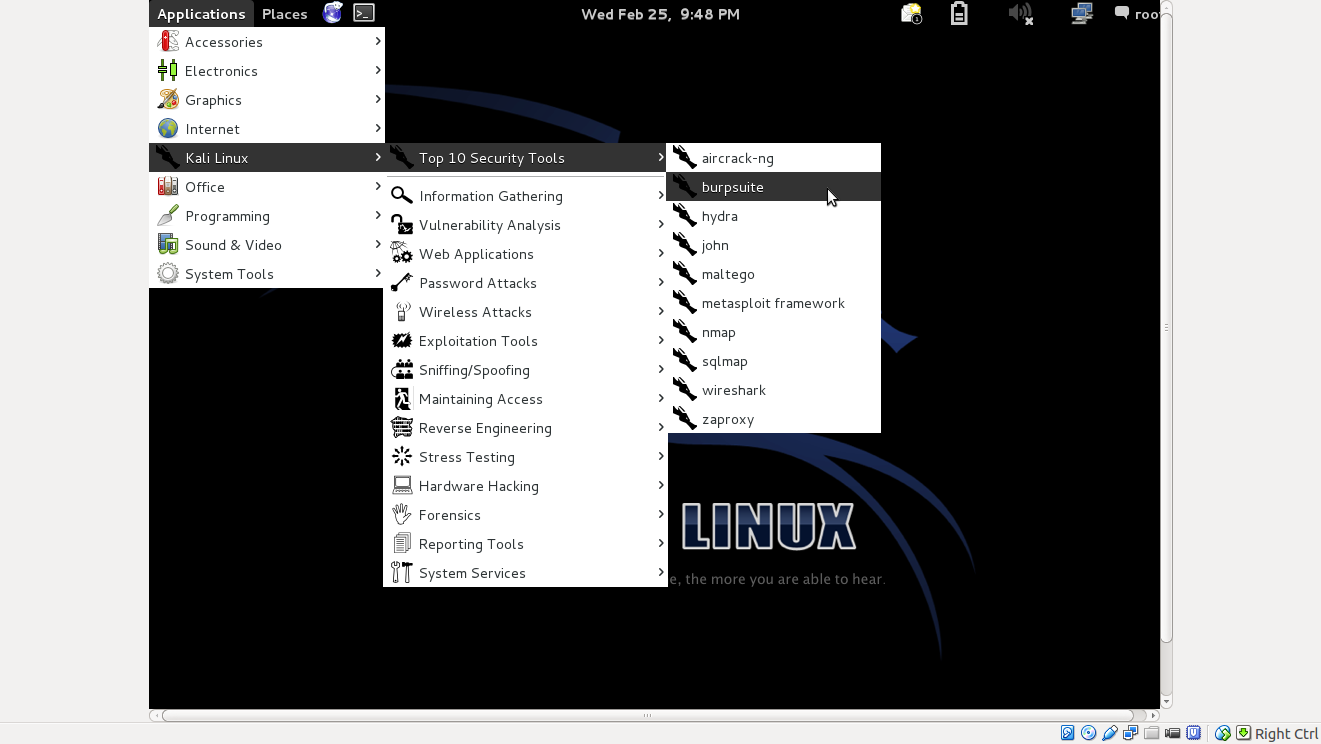
6. Now open burp suite Application → Kali Linux → Top 10 Security Tools → Burpsuite
7. You get to see the following screen
8. After Burp Suit is opened,Click on Proxy Tab then Click on Option Subtab and watch carefully local host interface running box should be check in Proxy Listeners.
9. Scroll down in the same tab (Proxy Tab → Option subtab)
Intercept Client Requests
→ Select URL Match type and keep Clicking UP button till URL Match type reach at the top.
→ Check Box 'Intercept requests based on the following rules.
Now select 'File Extension' and click on Edit.Edit Window will be open. Here we will add 'jpeg' file extension. You can add or remove file extension as per your need. So, Write code and click on OK.
10. We will Add file extension match type according to below details:
Boolean Operator : And
Match type : File Extension
Match relationship : Does not match
Match condition: (^gif$|^jpg$|^png$|^css$|^js$|^ico$|^jpeg$)
11. Select 'File extension' and keep Clicking UP button till 'File extension' reach at the 2nd top.
12. Now Open Iceweasel and type www.google.com in the web address area....and u r ON if all set right
Source of help : http://knoxd3.blogspot.in/2014/05/how-to-configure-burp-suite-with.html
Source of help : http://knoxd3.blogspot.in/2014/05/how-to-configure-burp-suite-with.html
 https://orcid.org/0000-0002-9097-2246
https://orcid.org/0000-0002-9097-2246