With this first post special to Bitcoin core,over next few months I intend to do some exploring on the bitcoin mechanics part.This basically means playing with the blocks and blockchain vide few python based scripts.Will start from the installation part followed by other posts on extracting info from bitcoin blockchain. This post basically is straight forward installation with the following commands.Screen shots for info :
Firstly install snapd with the following commands
sudo apt update
sudo apt install snapd
sudo apt install snapd
after this installation of snapd,one single command as follows:
sudo snap install bitcoin-core
The effected screenshots are seen below :
Once installed ,you can check on the terminal...should see three bitcoin applications by tabbing
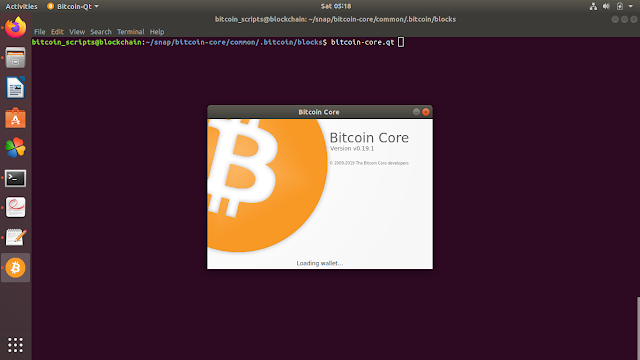
While the GUI shows as below
When you run for the first time,the GUI notification pops for asking for location of default directory for storing blocks.
Thereafter the blocks start getting downloaded with status of files downloaded visible....
Blocks downloaded status is seen below...this downloading around 287 GB as on date will take time as per download speed available.
The location of the blocks being downloaded will be at /home/bitcoin_scripts/snap/bitcoin-core/common/.bitcoin/blocks where bitcoin_scripts is the user name.
Next post we will see whats inside the block....
 https://orcid.org/0000-0002-9097-2246
https://orcid.org/0000-0002-9097-2246