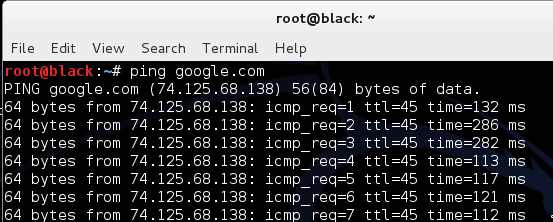
1. Most high-value targets have a DNS name associated to an application. DNS names make it easier for users to access a particular service and add a layer of professionalism to their system. For example, if you want to access Google for information, you could open a browser and type in 74.125.68.138 or type www.google.com
 |
| (Click on image to enlarge) |
2. DNS information about a particular target can be extremely useful to a Penetration Tester. DNS allows a Penetration Tester to map out systems and subdomains. To use Dig, open a command prompt and type dig and hostname, where hostname represents the target domain.
3. Dig lookups will show the DNS records for the given host or domain. This gateway allows lookups for network address, mail exchanger, name servers, host information, arbitrary strings and zone of authority records. Please leave the server field blank to query a properly configured internet DNS cache.Dig will use your operating systems default DNS settings to query the hostname.You can also configure Dig to query custom DNS servers by adding @ to the command. The example in the following screen shot illustrates using Dig on http://www.hacklabs.com/
4. The -t option in Dig will delegate a DNS zone to use the authoritative name
servers. We type dig -t ns http://www.hacklabs.com/ in the example in the
following screen shot:
servers. We type dig -t ns http://www.hacklabs.com/ in the example in the
following screen shot:
5. We see from the results we have two authoritative DNS servers for the domain http://www.hacklabs.com/; they are ns51.domaincontrol.com and ns51.domaincontrol.com
 https://orcid.org/0000-0002-9097-2246
https://orcid.org/0000-0002-9097-2246




















