1. Often when we discuss about encrypting messages in emails we see it is generally confined to PGP extensions using Thunderbird, exchanging public keys and generating private keys and other encryption techniques incl Enigmail or installing GPG etc...but even after doing all this the whole thing is a bit complicated ....and no one likes complications....so when techies get complicated...it actually becomes kind of out of bounds for the common user anyway to use encryption in routine mails with each other.But with increasing rise in concern over security and privacy matters by the common user specially after Snowden revelations,the need has given us PROTONMAIL.
2. PROTONMAIL This new encrypted email service, called ProtonMail is a super-secure email service created in collaboration with the scientists from Harvard, the Massachusetts Institute of Technology and the European research lab CERN.It offers a user-friendly experience with full “end-to-end” encryption and encrypts the data on the browser before it communicates with the server, therefore only encrypted data is stored in the email service servers. So, even if someone gains complete access to the server, it will find only the encrypted data. Moreover, there is even a “self-destruct” feature in the email service which ensures your emails are only available for a limited period of time.Isn't it interesting?....
3. At Protonmail,the decryption uses a combination of asymmetric (RSA) and symmetric (AES) encryption.So we have two cases wherein the user sends a mail from a Protonmail account to another user with Protonmail account and the other in which he sends a mail message to a non Protonmail user....
- For Protonmail to Protonmail emails, implementation of PGP is used where key exchange is handled. So we have all the public keys. As for the private keys, when an account is created, it is generated on the browser, then encrypted with your mailbox password (which we do not have access to). Then the encrypted private key is pushed to the server so it can push it back to user whenever he/she logins.
- For PM to Outside emails, encryption is optional. If one selects to encrypt, it uses symmetric encryption with a password that one can set for that message. This password can be ANYTHING. It should NOT be the Mailbox password. It needs to be somehow communicates to the recipient....few useful screenshots seen below :
This is the screen at LOGIN
Here you LOGIN
Here is the second password before you finally LOGIN to the user interface
Here is as you LOGIN
This is the screen as you compose a mail.The point to be seen is the feature for choosing to encrypt your message and the expiration time.
This is the mail received to a non PROTONMAIL user and we see there is a mail link it refers to!!!
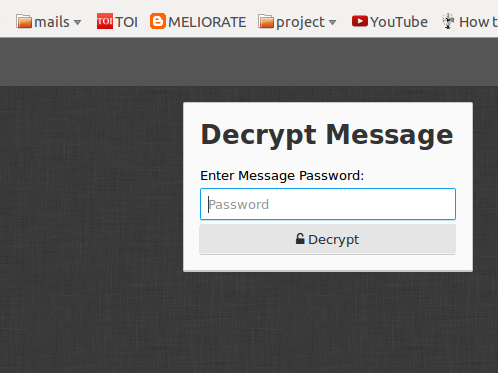
Once you click that link..you get a pop up for a password
You enter the password and you will be able to decipher the password.
3. At Protonmail,the decryption uses a combination of asymmetric (RSA) and symmetric (AES) encryption.So we have two cases wherein the user sends a mail from a Protonmail account to another user with Protonmail account and the other in which he sends a mail message to a non Protonmail user....
- For Protonmail to Protonmail emails, implementation of PGP is used where key exchange is handled. So we have all the public keys. As for the private keys, when an account is created, it is generated on the browser, then encrypted with your mailbox password (which we do not have access to). Then the encrypted private key is pushed to the server so it can push it back to user whenever he/she logins.
- For PM to Outside emails, encryption is optional. If one selects to encrypt, it uses symmetric encryption with a password that one can set for that message. This password can be ANYTHING. It should NOT be the Mailbox password. It needs to be somehow communicates to the recipient....few useful screenshots seen below :
This is the screen at LOGIN
Here you LOGIN
Here is the second password before you finally LOGIN to the user interface
Here is as you LOGIN
This is the screen as you compose a mail.The point to be seen is the feature for choosing to encrypt your message and the expiration time.
This is the mail received to a non PROTONMAIL user and we see there is a mail link it refers to!!!
Once you click that link..you get a pop up for a password
You enter the password and you will be able to decipher the password.
 https://orcid.org/0000-0002-9097-2246
https://orcid.org/0000-0002-9097-2246