1. Graylog2 is a powerful log management
and analysis tool that has many use cases, from monitoring SSH logins
and unusual activity to debugging applications. It is based on
Elasticsearch, Java, MongoDB, and Scala.The installation is not exactly to say simple since a lot of integration goes behind involving different applications including Elasticsearch, Java, MongoDB, and Scala. But in few steps and little modifications in default configuration files,the same can be run with ease.
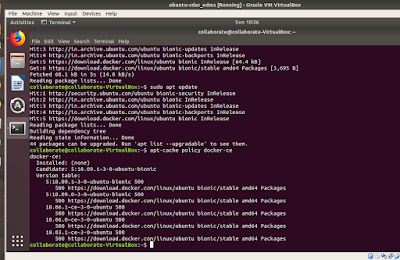
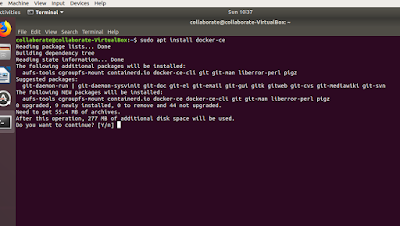
2. Below are terminal commands with screen shots to achieve the same running
Firstly,the system that I m installing the GRAYLOG on ..the specs are as below
Then coming to the root terminal...from where all the commands will be executed for installation.
$ apt update && apt upgrade
$ apt install apt-transport-https uuid-runtime pwgen openjdk-8-jre-headless
This is followed by installing ELASTICSEARCH
$ wget -qO - https://artifacts.elastic.co/GPG-KEY-elasticsearch | apt-key add -
$ echo "deb https://artifacts.elastic.co/packages/5.x/apt stable main" | sudo tee -a /etc/apt/sources.list.d/elastic-5.x.list
Next we install
$ apt update && apt install elasticsearch
This is followed by enabling the service and starting
$ systemctl enable elasticsearch
$ systemctl start elasticsearch
|
Amend cluster.name as graylog
Followed by these lines at the EOF
script.inline: false
script.indexed: false
script.file: false
This is followed by
$ systemctl restart elasticsearch
Now install the key
$ apt-key adv --keyserver hkp://keyserver.ubuntu.com:80 --recv 2930ADAE8CAF5059EE73BB4B58712A2291FA4AD5
Then MANGODB repository$ echo "deb [ arch=amd64,arm64 ] https://repo.mongodb.org/apt/ubuntu xenial/mongodb-org/3.6 multiverse" | sudo tee /etc/apt/sources.list.d/mongodb-org-3.6.list
Install mongodb
$ apt update && apt install mongodb-org
$ systemctl start mongod
$ systemctl enable mongod
$ wget https://packages.graylog2.org/repo/packages/graylog-2.5-repository_latest.deb $ dpkg -i graylog-2.5-repository_latest.deb $ apt-get update $ apt-get install graylog-server
After installation of the Graylog package is finished, we need
to edit the configuration file to set our password in it and we do it using pwgen command
$ pwgen -N 1 -s 96
$ echo -n your_password | sha256sum
We place the above generated output in the conf file as seen below :
Assistance reference from https://www.osradar.com/how-to-install-graylog-on-ubuntu-18-04/ - Thanks
 https://orcid.org/0000-0002-9097-2246
https://orcid.org/0000-0002-9097-2246