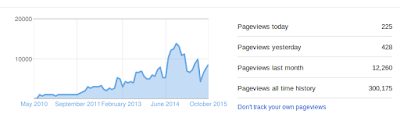
Exactly about a year back my blog got the 2,00,000th hit and today it is 3,00,000 plus.
So I assume an ok traffic since technical blogs do
not have the glamorous and mass factor associated....I got into blogging
without knowing any thing about traffic and readers
and then maintaining a blog when you are working also is at times
difficult.This actually means the time you could have spent with your
family is being spent on blogging.But then as we say "Purpose is the reason you journey and Passion is the fire that lights your way."...and
so has been applicable to me.Simply the passion to study and share IT
and experiment with tools and researches has been the force for my
energies being put in here.Putting here some past shots and analytics ex Google :
Tuesday, October 20, 2015
Sunday, October 04, 2015
Extracting Username/Passwords from RAM Dump : Volatility Framework makes it Easy
1. For those of you who have started reading this post coz of the tempting post title claiming extracting username/passwords from a RAM Dump,I must assure you it is possible easily in few steps using Volatility Framework.In the post ahead I have a RAM dump of a Windows 7 OS and I have been able to extract the user names and passwords of these users in three simple steps using Volatility Framework.Well,I will quickly get to the steps with screenshots :
Setup Required
- Volatility Framework Installed.[How to Install at http://anupriti.blogspot.in/2015/09/volatility-advanced-memory-forensics.html]
- Taking Ram Dump from Windows
[How to take RAM dump at para 3 of http://anupriti.blogspot.in/2015/09/volatility-command-using-imageinfo-to.html]
Here I am using two commands basically ie hivelist and hashdump
HIVELIST
Hivelist is used to locate the virtual addresses of registry hives in memory, and the full paths to the corresponding hive on disk.
Command Usage
python vol.py --profile=Win7SP0x86 -f /home/cuckoo/Desktop/windows_7_ramdump.raw hivelistYou get a similar output as seen below :
 |
| CLICK TO ENLARGE |
 |
| Note Virtual Address for SYSTEM as highlighted CLICK TO ENLARGE |
 |
| Note Virtual Address for SAM as highlighted CLICK TO ENLARGE |
HASHDUMP
Hashdump is used to extract and decrypt cached domain credentials stored in the registry.
Command Usage
To use hashdump, pass the virtual address of the SYSTEM hive as -y and the virtual address of the SAM hive as -s, as shown below:python vol.py --profile=Win7SP0x86 hashdump -f /home/cuckoo/Desktop/windows_7_ramdump.raw -y 0x8901a360 -s 0x8faff008
 |
| Hashdump output seen with user names and NTLM dump CLICK TO ENLARGE |
DECRYPTING NTLM hash
Now comes decrypting this hash as we have got vide hashdump above.Hashes can now be cracked using John the Ripper, rainbow tables, etc.Now no need to install these crackers separately.Simply google for online decryptos and you will get the password too.I used this site at http://www.hashkiller.co.uk/ntlm-decrypter.aspxScreen shots below:
 |
| Password extracted is test_1234 CLICK TO ENLARGE |
 |
| Password extracted is test_123 CLICK TO ENLARGE |
 |
| Password extracted is test CLICK TO ENLARGE |
Thursday, October 01, 2015
Burp Suite : Configuring the browser and redirecting traffic
1. Vide my last post about installing Burp Suite here ,now I move ahead to configure your browser in order to redirect all HTTP/S requests through Burp Proxy, instead of the actual target website. In my case here I am configuring a Mozilla Browser with proxy host address to 127.0.0.1 and the proxy port to 8080 , for both HTTP and HTTPS.The typical configuring of browsers is more or less common with major browsers with minor differences in interfaces.Here next I place you screen shots as I surfed a redirected traffic both for http and https via Burp Suite.First steps to configure Mozilla followed by screen shots :
Configuring Mozilla Firefox
- Click Firefox menu and then Preferences.
- In the Advanced options, under the Network tab, click on connection Settings.
- Select Manual proxy configuration.
- Enter the proxy host address as 127.0.0.1 and the proxy port as 8080.
- Select Use this proxy server for all protocols.
- Make sure to remove all exceptions from the No Proxy for field.
- Click OK and close.
- In the Advanced options, under the Network tab, click on connection Settings.
- Select Manual proxy configuration.
- Enter the proxy host address as 127.0.0.1 and the proxy port as 8080.
- Select Use this proxy server for all protocols.
- Make sure to remove all exceptions from the No Proxy for field.
- Click OK and close.
2. So now you have a working installation of Burp Suite and your browser is properly configured to intercept all requests.Now to test go to the browser, enter any http://www.****** site in the address bar and press Enter . If all is well, Burp Proxy should intercept this request. In Burp Suite,go to the Proxy and Intercept tab and verify that the web request is waiting for your approval.Ensure tha the Intercept on button is enabled; click on it and allow the request to transit through Burp by pressing Forward in Burp Suite Interface. Now in the browser, you should see the http page you entered in address bar.
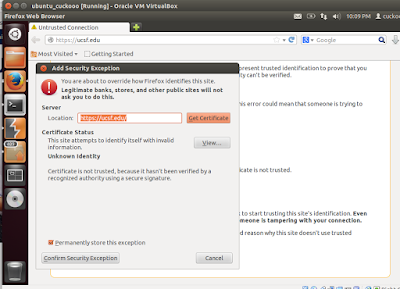
Now try a https site and you are bound to see this warning as seen below in the screenshot.You will be presented with a This Connection is Untrusted page.In such a case, you are required to manually approve the connection by clicking on I Understand The Risks, then Add Exceptions... and Confirm Security Exception. To make sure that Burp Proxy is actually causing the warning, you click on the certificate status View... and see that the certificate belongs to PortSwigger CA as seen below in one screenshot.
PortSwigger CA certificate
This setup means that Burp Suite is now ready for use as the traffic is being redirected as desired as per configuration....
Labels:
burp suite,
burpsuite,
CYBER ATTACK,
cyber awareness,
cyber forensic,
cyber security,
Hack Tools,
http,
HTTPS,
mozilla,
Open source,
screenshots,
ubuntu,
web application security
Monday, September 28, 2015
Burp Suite : Integrated platform for Web Application Security
1. Burp Suite is an excellent easy-to-use integrated platform for web application security that includes multiple tools seamlessly integrated to test every component and aspect of modern web applications. Whether you need to verify the robustness of your authentication mechanism, the predictability of your session tokens, or the input validation checkpoints present in your application, Burp is often compared to Swiss-army knife for security practitioners since it offers a horde of features . Not only does it allow in-depth manual assessments, but it also combines automated techniques to enumerate and analyze web application resources.Burp has been developed by PortSwigger Ltd. and is available in two editions:
- Burp Free
- Burp Professional
In-fact,the free version is perfect to start for beginners as it contains all the basic tools to find at least few first vulnerabilities.In its simplest way to explain, Burp is a local web proxy that allows to intercept, inspect, and modify HTTP/S requests and responses between the user's browser and the target website. While the user navigates through the web application, the tool acquires details on all visited pages, scripts,parameters, and other components. The traffic between the browser and the server can be eventually visualized, analyzed, modified, and repeated multiple times. The different tools included in Burp Suite can be easily distinguished by the upper tabs:
- Proxy: It allows to intercept and modify all web traffic.
- Target: This tool allows to aggregate all web application resources, thus guiding the user throughout the security test.
- Scanner: A complete web application security scanner, available in the Professional version only.
- Intruder: Burp Intruder allows to customize and automate web requests.
- Spider: Automatic crawler that can be used to discover new pages and parameters.
- Sequencer: Used for verifying the randomness and predictability of security tokens, cookies, and more.
- Decoder: It allows to encode and decode data using multiple encoding schemes
- Comparer: A visual diff tool that can be used to detect changes between web pages.
- Repeater: A simple yet powerful tool that can be used to manually modify and re-issue web requests.
How to go about Installation ?
- A minimum disk space of at least 200 MB is required.
- Required memory is at least 1 GB
- Burp Suite works on Windows, Mac OS X, and Linux
- Software components: An updated Oracle Java Runtime Environment is required to run Burp Suite.
Downloading Burp Suite from ?
Download link at http://www.portswigger.net/burp/download.html
In the download folder where typically this file gets downloaded,create a burpsuite folder and mov this file to this folder for executing.
Launching Burp Suite in Linux
At the terminal type the following inside the pwd as the new burpsuite folder u created above :
java -Xmx2g -jar burpsuite_v1.4.01.jar
Volatility Framework Command : Using dlllist - dlldump to extricate DLLfile details
This post will share an example to run the two volatility terminal commands including dllllist and dlldump to display a process's loaded DLLs.
Before I proceed ahead,I would assume that you have installed volatility
in your Linux system(in my case I am using UBUNTU, Installation
explained at my earlier post at http://anupriti.blogspot.in/2015/09/volatility-advanced-memory-forensics.html)
and you have a RAM dump of the OS u desire to analyse.In my case here I
have taken the RAM dump of a Windows 7 OS as explained here at http://anupriti.blogspot.in/2015/09/volatility-command-using-imageinfo-to.html
dlllist
dlllist is used to display a process's loaded DLLs.DLLs are automatically added to this list when a process calls LoadLibrary (or some derivative such as LdrLoadDll).vol.py --profile=Win7SP0x86 -f windows7_image.raw dlllist
To display the DLLs for a specific process instead of all processes, there is option to use the switch -p or --pid filter as shown below:
vol.py --profile=Win7SP0x86 -f windows7_image.raw dlllist --pid=1892
To display the DLLs for a process that is hidden or unlinked by a rootkit, first use the psscan to get the physical offset of the EPROCESS object and then:
vol.py --profile=Win7SP0x86 -f windows7_image.raw dlllist --offset=0x04a291a8
 |
| (Click on the image to ENLARGE) |
dlldump
dlldump command is used to extract a DLL from a process's memory space and dump it to disk for analysis.The syntax is nearly the same as what has been seen earlier with any command.This plugin provisions the following :- Dump all DLLs from a hidden/unlinked process (with --offset=OFFSET)
- Dump all DLLs from a specific process (with --pid=PID)
- Dump all DLLs from all processes
- Dump a PE from anywhere in process memory (with --base=BASEADDR), this option is useful for extracting hidden DLLs
To specify an output directory, use --dump-dir=DIR or -d DIR.
vol.py --profile=Win7SP0x86 -f windows7_image.raw dlldump --dump-dir output
where output is the name of directory where u get the dll dump
the output directory will be seen as seen below :
More at : https://code.google.com/p/volatility/wiki/CommandReference#dlllist
Labels:
cyber forensic,
cyber security,
dll dump,
dlllist,
dumpit,
Linux,
memory forensics,
OPENSOURCE,
operating system,
Penetration Tester,
ram dump,
virtual box,
volatility,
windows
Subscribe to:
Posts (Atom)
 https://orcid.org/0000-0002-9097-2246
https://orcid.org/0000-0002-9097-2246