Sharing this presentation here in this post that brings an exhaustive overview of the Blockchain Technology and emerging Cryptocurrencies crimes.The presentation was given at CBI Academy on 16 Nov 18 by self :
Saturday, November 17, 2018
Sunday, September 09, 2018
Aadhaar on Blockchain : Consider or not? - Post 1/2
[This post builds upon introducing Aadhaar,its size,current way of handling the data sets,discuss its problems and subsequently followed by proposing Blockchain as a solution]
1. When Aadhaar was originally introduced around 2009-10 by the Unique Identification Authority of India (UIDAI),it would not have envisaged the kind of Data juggling,analytics and security threats it would be subjected to in times to come.And here we are around the third quarter of 2018,wherein Aadhaar is central to so many authentications in the country ,being exploited in so many public utility services and also at the same time being subjected to all kind of threats and claims of data theft and leaks.For a record,it is estimated that around 1.2 billion citizens record are held in the CENTRAL servers and thus forms the worlds largest bio-metric identity repository in the world.UIDAI claims that the same is protected by layers of state of art cryptography in central servers located in the country.
2. Now in the world of IT,wherein claiming to be 100% secure is likely to remain a myth for ages ahead,can something like un-hackable really exist on this earth? We may harden something,we may actually add layers of security, we may do every possible hard encryption on this earth,but can we imagine a fool-proof IT domain anywhere. The question here attains severe importance when a Bio-metric repository data of 1.2 billion plus population of a country is at stake.
3. Now what do we have on the platter here,if we consider the size of data,we can have the following assumptions :
(a) Per person biometric data size : 4-6 MB (Maximum I take)
(b) Approx data populated for : Around 1.25 billion plus ie 1,250,000,000 count
Total data ie to say 6 MB x 1,250,000,000 = 7500000000 MB Data ie around 7.5 Petabyte.....that's it...extrapolate the same with on-site backup and mirrors around...disaster recovery sites...we may just be discussing around 20 PB of data.
Even if we consider,augmenting data with the remaining population and generations ahead,we will be at max around 40-45PB of data to suffice around next few decades.That's all from point of view of the scalability of data and size.
4. Now for this amount data, what are our security options in the present scenario.
Firstly we keep doing permutations and combinations and applying layers of hard coded security to the central servers that we have at various locations mirrored to each other.This presently includes the following : [SOURCE : http://www.cse.iitd.ernet.in/~suban/reports/aadhaar.pdf]
- 2048 bit PKI encryption of biometric data in transit. End-to-end encryption from enrollment/POS to CIDR.
- Trusted network carriers.
- Trusted network carriers.
- Effective precaution against denial of service (DOS) attacks.
- HMAC(keyed-hash message authentication code) based tamper detection of PID (Personal Identity Data) blocks, which encapsulate bio-metric and other data at the field devices.
- Registration and authentication of AUAs.
- Within CIDR only a SHA-n Hash of Aadhaar number is stored.
- Audit trails are stored SHA-n encrypted, possibly also with HMAC based tamper detection.
- Only hashes of passwords and PINs are stored.
- HMAC(keyed-hash message authentication code) based tamper detection of PID (Personal Identity Data) blocks, which encapsulate bio-metric and other data at the field devices.
- Registration and authentication of AUAs.
- Within CIDR only a SHA-n Hash of Aadhaar number is stored.
- Audit trails are stored SHA-n encrypted, possibly also with HMAC based tamper detection.
- Only hashes of passwords and PINs are stored.
- Biometric data are stored in original form though.
- Authentication requests have unique session keys and HMAC.
- Authentication requests have unique session keys and HMAC.
- Protection against replay attacks.
- Resident data stored using 100 way sharding (vertical partitioning).First two digits of Aadhaar number are used as shared keys.
- All system accesses, including administration, through a hardware security module (HSM) which maintains an audit trail.
- All analytics carried out only on anonymized data.
- Resident data stored using 100 way sharding (vertical partitioning).First two digits of Aadhaar number are used as shared keys.
- All system accesses, including administration, through a hardware security module (HSM) which maintains an audit trail.
- All analytics carried out only on anonymized data.
From the IT guys perspectives,don't we actually know that above are all individual knitted layers and tools of security wherein we are creating a very complex network of solution for ourselves which might get even more complex to handle and manage in times to come with more severe security threats in pipelines.
At the same time, above all solutions and knits combinations are looking and bracing for external threats while we take the insider threats as negligible or taken for granted any day.
So do we have any other ecosystem of architecture that turns the tables upside down from the security and immutability point of view while OFFERING A MORE ROBUST SECURE IMMUTABLE AND TRANSPARENT ARCHITECTURE...whether BLOCKCHAIN can be a solution?
So,we have the above scenario which discusses what do we have on the platter and what are we actually doing to negate the threats....the next post will discuss how BLOCKCHAIN can assist to negate the security threats Aadhaar faces as on date.
Monday, April 02, 2018
Bitcoin Address Generation : The Internals Behind
ECDSA stands for Elliptic Curve Digital Signature Algorithm and uses an
elliptic curve and a finite field to "sign" data in such a way that
third parties can verify the authenticity of the signature while the
signer retains the exclusive ability to create the signature. The Bitcoin addressing system is not a simple deal.In order to maintain that a public key cannot be deciphered easily to any identity and in future if ECDSA is compromised at all, still,the anonymity remains.So suppose you have a ECDSA based private key,the following post content will give a step by step sequence of how the final bitcoin address is derived :
Sequence flow chart is shown below :
 |
| Image courtesy : https://www.safaribooksonline.com/library/view/mastering-bitcoin-2nd/9781491954379/assets/mbc2_0405.png |
Your sample private key :
18E14A7B6A307F426A94F8114701E7C8E774E7F9A47E2C2035DB29A206321725
Public key derived is
0450863AD64A87AE8A2FE83C1AF1A8403CB53F53E486D8511DAD8A04887E5B2
3522CD470243453A299FA9E77237716103ABC11A1DF38855ED6F2EE187E9C582
BA6
Site reference : https://www.bitaddress.org
Screen shot below :
Now perform SHA-256 hashing on the hex of the public key as shown below in the screenshot :
The SHA-256 output received is
600ffe422b4e00731a59557a5cca46cc183944191006324a447bdb2d98d4b408
Now we take RIPEMD-160 Hash of the above output and get this as follows as seen vide the screenshot :
010966776006953d5567439e5e39f86a0d273bee
Now add Add version byte in front of RIPEMD-160 hash (0x00 for Main Network).so that the above output becomes :
00010966776006953D5567439E5E39F86A0D273BEE
Further to above,Perform SHA-256 hash on the extended RIPEMD-160 result ie
so we get
445c7a8007a93d8733188288bb320a8fe2debd2ae1b47f0f50bc10bae845c094
445c7a8007a93d8733188288bb320a8fe2debd2ae1b47f0f50bc10bae845c094
and now we perform SHA-256 hash on the result of the this recent SHA-256 hash as seen below in the screenshot...and we get this as
d61967f63c7dd183914a4ae452c9f6ad5d462ce3d277798075b107615c1a8a30
Now take the first 4 bytes of the second SHA-256 hash and this is the address checksum ie D61967F6
and then add the 4 checksum bytes at the end of extended RIPEMD-160
hash as hashed above and we get the 25-byte binary Bitcoin Address.
00010966776006953D5567439E5E39F86A0D273BEED61967F6
Now the last step...we Convert the result from a byte string into a base58 string using Base58Check encoding at https://incoherency.co.uk/base58/
Bitcoin Address :
16UwLL9Risc3QfPqBUvKofHmBQ7wMtjvM
Useful links :
Friday, March 30, 2018
Compiling Bitcoin Core Source Code : Ubuntu 16.04 LTS
1. Bitcoin Core is the reference implementation of bitcoin and anyone ON
with any projects around bitcoin would need to compile the bitcoin
source code to create the bitcoind for his/her own node. Ubuntu is usually the operating system recommended to run Bitcoin Core.This post will build upon with screenshots as done and terminal commands as executed to compile the same vide GIT.
2. The machine I have used here is a Ubuntu 64 bit running on a virtual box platform with the following details as seen in the screenshot :
Now on I will just share the terminal commands as i executed in the terminal :
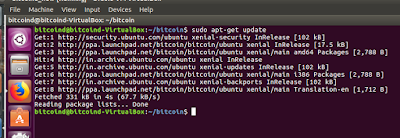
sudo apt-get update
sudo apt-get upgrade

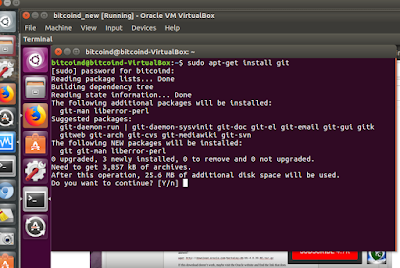
sudo apt-get install git
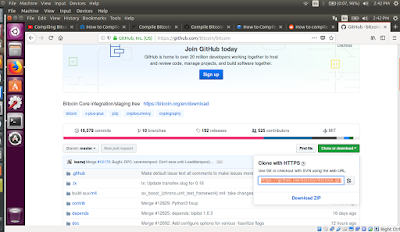
Search for Bitcoin github and click the first link as seen below :
Goto the link as seen below at https://github.com/bitcoin/bitcoin/blob/master/doc/build-unix.md
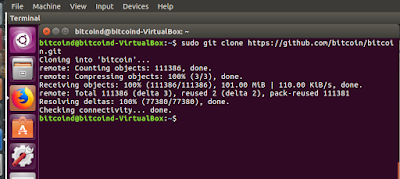
sudo git clone https://github.com/bitcoin/bitcoin.git
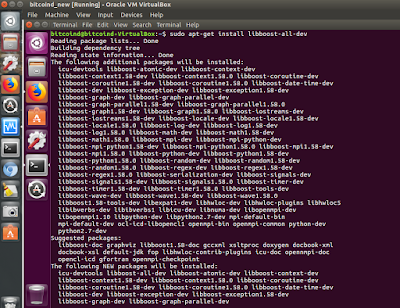
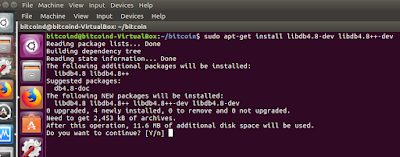
sudo apt-get install build-essential libtool autotools-dev automake pkg-config libssl-dev libevent-dev bsdmainutils python3
sudo apt-get install libboost-system-dev libboost-filesystem-dev libboost-chrono-dev libboost-program-options-dev libboost-test-dev libboost-thread-dev
sudo apt-get install libboost-all-dev
sudo apt-get install software-properties-common
sudo add-apt-repository ppa:bitcoin/bitcoin
sudo apt-get update
sudo apt-get install libdb4.8-dev libdb4.8++-dev
sudo apt-get install libminiupnpc-dev
sudo apt-get install libzmq3-dev
sudo apt-get install libqt5gui5 libqt5core5a libqt5dbus5 qttools5-dev qttools5-dev-tools libprotobuf-dev protobuf-compiler
sudo apt-get install libqrencode-dev
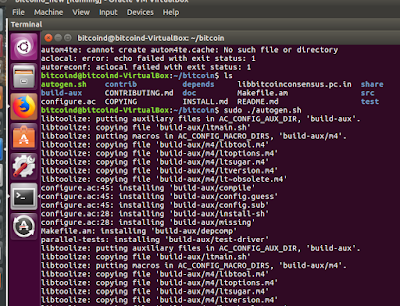
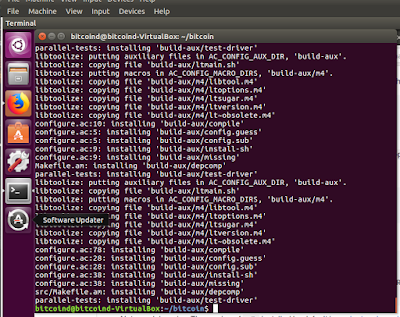
sudo ./autogen.sh
sudo ./configure --disable-wallet #
sudo make
and the last command
sudo make install
....and you r ready to go.....
Saturday, March 24, 2018
The MIST Browser : Installation UBUNTU 16.04 LTS
Mist Browser (formerly Ethereum Dapp Browser) is the end-user interface for Ethereum. It's the tool of choice for browsing and using Dapps and is specifically designed for non-technical users.The following post shows a series of screen shots to install the same on UBUNTU 16.04 LTS.Zoom in the screen shots to see the details as desired please. Link at
https://github.com/ethereum/mist/releases
https://github.com/ethereum/mist/releases

Monday, March 19, 2018
BLOCKCHAIN ,BITCOIN & CRYPTOCURRENCIES WORLD : MECHANICS AND CYBER CRIME
The world of Blockchain and Cryptocurrencies is undeniably amazing and has infinity to explore at hands.Recently I took on a 4 hour session at the prestigious Central Bureau of Investigations,CBI Academy ,Ghaziabad, vide Indian Technical and Economic Cooperation Programme organised by Ministry of External Affairs,to cover right from scratch to overview of mechanics and architecture of how this world works.Sharing here the presentation for info and awareness of anyone who is interested to take a dip in this domain and related cyber crime activities.
Subscribe to:
Posts (Atom)
 https://orcid.org/0000-0002-9097-2246
https://orcid.org/0000-0002-9097-2246